How to connect to the WPA2 EAP-TLS network: Unterschied zwischen den Versionen
aus Metalab Wiki, dem offenen Zentrum für meta-disziplinäre Magier und technisch-kreative Enthusiasten.
Zur Navigation springenZur Suche springenRa (Diskussion | Beiträge) K (restructure) |
Ra (Diskussion | Beiträge) (→Linux: NetworkManager) |
||
| Zeile 10: | Zeile 10: | ||
== Use certificates == | == Use certificates == | ||
=== Linux === | === Linux === | ||
| + | |||
| + | ==== wpa_supplicant ==== | ||
sample wpa_supplicant.conf:<br> | sample wpa_supplicant.conf:<br> | ||
network={ | network={ | ||
| Zeile 26: | Zeile 28: | ||
} | } | ||
| + | |||
| + | ==== NetworkManager ==== | ||
| + | Use ''yourname'' as identity, ''ca.crt'' as ca-certificate, ''yourname-cert.pem'' as client-certificate (with NetworkManager-0.7 you may need to use ''yourname-cert.p12'' instead) and ''secretpassword'' as key-password. | ||
=== MacOS X === | === MacOS X === | ||
Version vom 28. Februar 2009, 23:32 Uhr
Create certificates
You need to create/use a certificate to connect to the WPA2 access point.
- connect to the unencrypted wireless network metalab-wpa2-certcreation
- open your browser and go to https://10.215.23.1
- create the certificate by entering a hostname and password
You are now able to connect to the network by using the ca and your client certificate.
Use certificates
Linux
wpa_supplicant
sample wpa_supplicant.conf:
network={
ssid="metalab-wpa2"
scan_ssid=1
key_mgmt=WPA-EAP
proto=WPA2
eap=TLS
pairwise=CCMP
group=CCMP
identity="yourname"
ca_cert="/path/to/ca.crt"
client_cert="/path/to/yourname-cert.pem"
private_key="/path/to/yourname-key.pem"
private_key_passwd="secretpassword"
}
NetworkManager
Use yourname as identity, ca.crt as ca-certificate, yourname-cert.pem as client-certificate (with NetworkManager-0.7 you may need to use yourname-cert.p12 instead) and secretpassword as key-password.
MacOS X
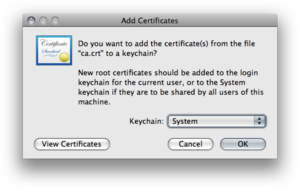
Import the ca-certifcate "ca.crt" to the system keychain.
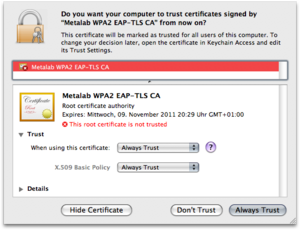
Set the trust level for the ca-certificate
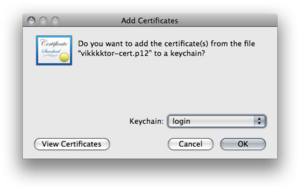
Import the client certifcate "yourname-cert.p12" to the login keychain with the choosen import password.
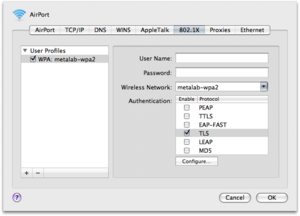
Connect to the metalab-wpa2 network
Windows
tbd
Manual server side setup
Create a certificate
## connect to wpa-01.in.metalab.at (10.20.30.25) as root. # user@host:~# ssh -l root wpa-01.in.metalab.at # root@wpa-01:~# ./mkclient.sh hostname password # root@wpa-01:~# exit ## copy the certificates to your host # user@host:~# scp -r root@wpa-01.in.metalab.at:/tmp/yourname.tar /path/to
Revoke certificate
## connect to wpa-01.in.metalab.at (10.20.30.25) as root. # user@host:~# ssh -l root wpa-01.in.metalab.at # root@wpa-01:~# cd /ca # root@wpa-01:~# ./revoke.sh yourname ## enter ca password
Server documentation
tbd