How to connect to the WPA2 EAP-TLS network
Create certificates
You need to create/use a certificate to connect to the WPA2 access point.
- Connect to the unencrypted wireless network metalab_802.11g_WPA2-certcreate
- Open your browser and go to https://10.215.23.1/
Please verify the fingerprints to make sure that there is no man in the middle pretending to be webserver:
SHA1 E1:C4:0F:06:C9:0A:C0:71:D3:D5:75:73:C7:D8:ED:FD:E7:40:15:05
MD5 24:28:1F:FF:4F:E5:EA:47:A0:3A:FD:D4:0D:A0:8B:62 - Create the certificate by entering a hostname and password
You are now able to connect to the network by using the ca and your client certificate.
Use certificates
Linux
wpa_supplicant
sample wpa_supplicant.conf:
network={
ssid="metalab-wpa2"
scan_ssid=1
key_mgmt=WPA-EAP
proto=WPA2
eap=TLS
pairwise=CCMP
group=CCMP
identity="yourname"
ca_cert="/path/to/ca.crt"
client_cert="/path/to/yourname-cert.pem"
private_key="/path/to/yourname-key.pem"
private_key_passwd="secretpassword"
}
NetworkManager
Use yourname as identity, ca.crt as ca-certificate, yourname-cert.pem as client-certificate (with NetworkManager-0.7 you may need to use yourname-cert.p12 instead) and secretpassword as key-password.
MacOS X
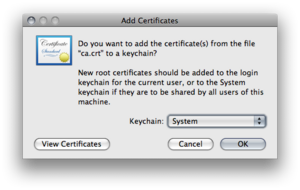
Import the ca-certifcate "ca.crt" to the system keychain.
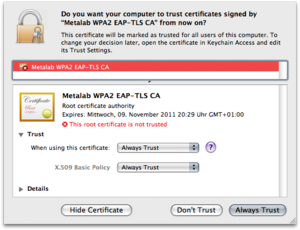
Set the trust level for the ca-certificate
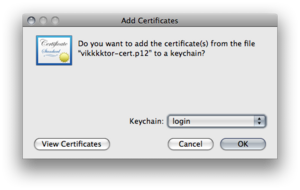
Import the client certifcate "yourname-cert.p12" to the login keychain with the choosen import password.
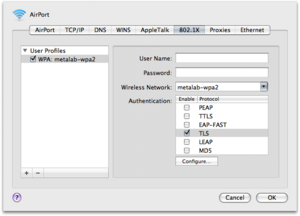
Connect to the metalab-wpa2 network
Windows
tbd
Manual server side setup
Create a certificate
## connect to wpa-01.in.metalab.at (10.20.30.25) as root. # user@host:~# ssh -l root wpa-01.in.metalab.at # root@wpa-01:~# ./mkclient.sh hostname password # root@wpa-01:~# exit ## copy the certificates to your host # user@host:~# scp -r root@wpa-01.in.metalab.at:/tmp/yourname.tar /path/to
Revoke certificate
## connect to wpa-01.in.metalab.at (10.20.30.25) as root. # user@host:~# ssh -l root wpa-01.in.metalab.at # root@wpa-01:~# cd /ca # root@wpa-01:~# ./revoke.sh yourname ## enter ca password
Server documentation
tbd